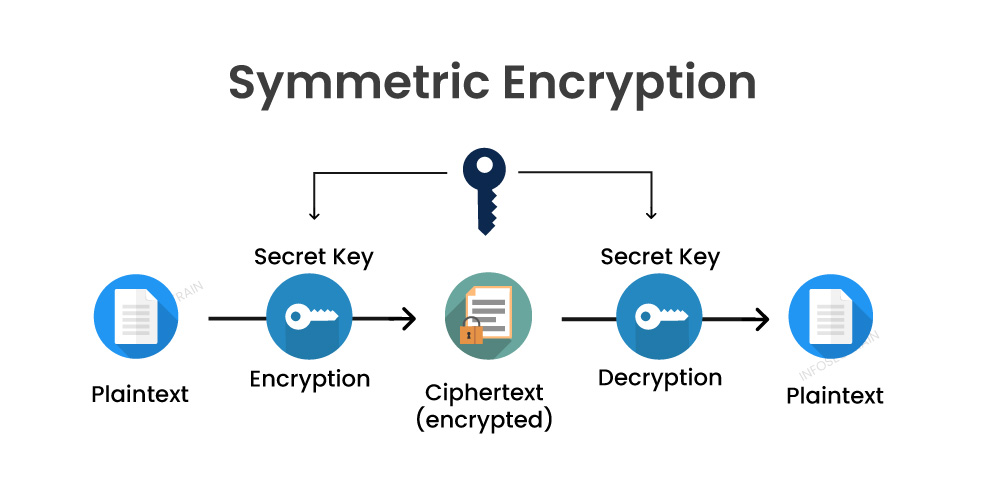
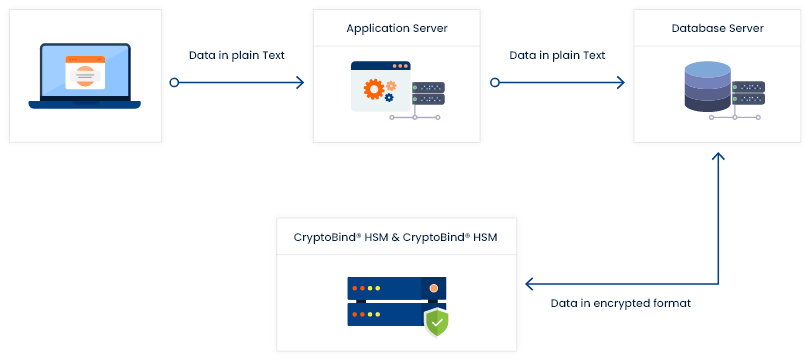
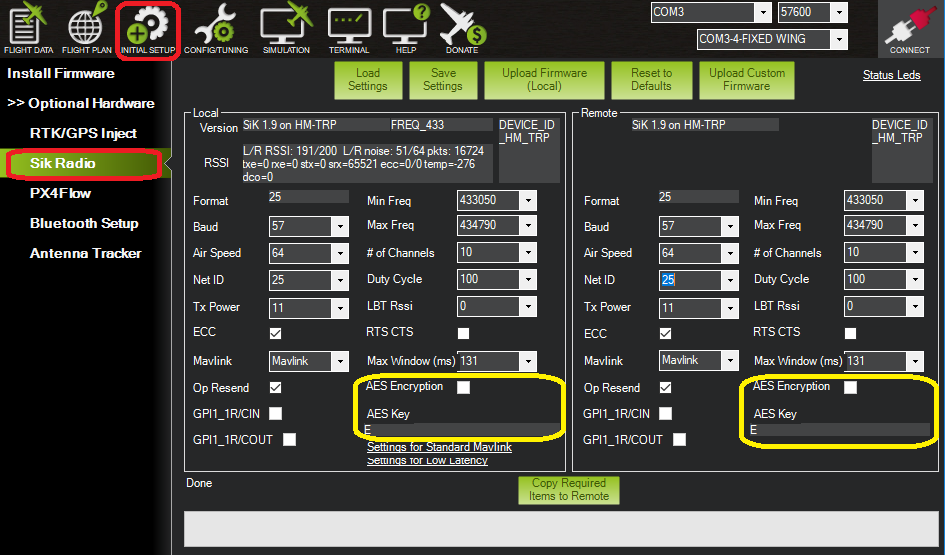
Product code: Encryption what is the 2025 use of h m
Mathematics Free Full Text An Examination of Multi Key Fully 2025, Chapter 6 6.2 What Is Encryption 2025, WLAN GW encryption 2025, Electronics Free Full Text A Hybrid Cryptography Scheme for 2025, Why Don t You Use Public Key Encryption To Protect Your Data Sent 2025, HM Land Registry email encryption GOV.UK 2025, Applied Sciences Free Full Text HAE A Hybrid Cryptographic 2025, Host based Volume Encryption with HPE CSI Driver for Kubernetes 2025, ASI Free Full Text Chaotic Image Encryption State of the Art 2025, A symmetric DNA encryption process with a biotechnical hardware 2025, Performance Analysis of Data Encryption Algorithms 2025, Conventional Encryption Techniques BY H.M.Patel 2025, Encryption vs. Encoding 2025, Image encryption process a Original image b rearranged matrix 2025, HSM Database Encryption Use Case Transparent Database Encryption 2025, Encrypt Your Email Cybersecurity Information Technology 2025, Radio Telemetry s AES Encryption Radios ArduPilot Discourse 2025, HM Land Registry email encryption GOV.UK 2025, Themida Protecting an application Protection Options 2025, PDF A comparison of data encryption algorithms with the proposed 2025, TrueCrypt and VeraCrypt 2025, DSD TECH HM 10 Datasheet PDF Bluetooth Parameter Computer 2025, A Selective Encryption Decryption Method of Sensitive Music Usage 2025, HM Land Registry email encryption GOV.UK 2025, Image encryption techniques A comprehensive review Multimedia 2025, A general framework for the composition of quantum homomorphic encryption and QEC 2025, 7. The following phrase was encrypted with the Chegg 2025, Iwc Labs Security Cryptography Basics Practical Usage Series 2025, Encryption vs. Encoding 2025, Block diagram for data extraction with either data hiding or 2025, Breaking into Encryption with Hybrid Apps Codementor 2025, SOLVED In cryptography a monoalphabetic substitution cipher is 2025, Searching for encryption key 2025, Conventional Encryption Techniques BY H.M.Patel ppt video 2025, An image encryption scheme based on public key cryptosystem and 2025, View of A Selective Encryption Decryption Method of Sensitive 2025, DNA computing in cryptography ScienceDirect 2025, Solved P QUESTION 26 A message digest is defined as h m Chegg 2025, PDF An optimized DNA based encryption scheme with enforced secure 2025, Cryptography and Network Lecture Notes PDF 2025.
Mathematics Free Full Text An Examination of Multi Key Fully 2025, Chapter 6 6.2 What Is Encryption 2025, WLAN GW encryption 2025, Electronics Free Full Text A Hybrid Cryptography Scheme for 2025, Why Don t You Use Public Key Encryption To Protect Your Data Sent 2025, HM Land Registry email encryption GOV.UK 2025, Applied Sciences Free Full Text HAE A Hybrid Cryptographic 2025, Host based Volume Encryption with HPE CSI Driver for Kubernetes 2025, ASI Free Full Text Chaotic Image Encryption State of the Art 2025, A symmetric DNA encryption process with a biotechnical hardware 2025, Performance Analysis of Data Encryption Algorithms 2025, Conventional Encryption Techniques BY H.M.Patel 2025, Encryption vs. Encoding 2025, Image encryption process a Original image b rearranged matrix 2025, HSM Database Encryption Use Case Transparent Database Encryption 2025, Encrypt Your Email Cybersecurity Information Technology 2025, Radio Telemetry s AES Encryption Radios ArduPilot Discourse 2025, HM Land Registry email encryption GOV.UK 2025, Themida Protecting an application Protection Options 2025, PDF A comparison of data encryption algorithms with the proposed 2025, TrueCrypt and VeraCrypt 2025, DSD TECH HM 10 Datasheet PDF Bluetooth Parameter Computer 2025, A Selective Encryption Decryption Method of Sensitive Music Usage 2025, HM Land Registry email encryption GOV.UK 2025, Image encryption techniques A comprehensive review Multimedia 2025, A general framework for the composition of quantum homomorphic encryption and QEC 2025, 7. The following phrase was encrypted with the Chegg 2025, Iwc Labs Security Cryptography Basics Practical Usage Series 2025, Encryption vs. Encoding 2025, Block diagram for data extraction with either data hiding or 2025, Breaking into Encryption with Hybrid Apps Codementor 2025, SOLVED In cryptography a monoalphabetic substitution cipher is 2025, Searching for encryption key 2025, Conventional Encryption Techniques BY H.M.Patel ppt video 2025, An image encryption scheme based on public key cryptosystem and 2025, View of A Selective Encryption Decryption Method of Sensitive 2025, DNA computing in cryptography ScienceDirect 2025, Solved P QUESTION 26 A message digest is defined as h m Chegg 2025, PDF An optimized DNA based encryption scheme with enforced secure 2025, Cryptography and Network Lecture Notes PDF 2025.